

Cybersecurity News You Can Use

The next time you come across an outrageous post on social media, take a moment to pause and think.
Scammers are using AI to create tens of thousands of fake political accounts on platforms like Facebook, X, and LinkedIn. These accounts post provocative content designed to provoke anger and manipulate real users.
According to TheHackerNews, these campaigns often originate from foreign actors aiming to cause division, political groups trying to influence opinion, and cybercriminals testing ways to profit from engagement.
AI technology is making it easier to generate convincing, emotionally charged comments — even in native languages the scammers don’t speak, and automated tools then flood online conversations with these posts.
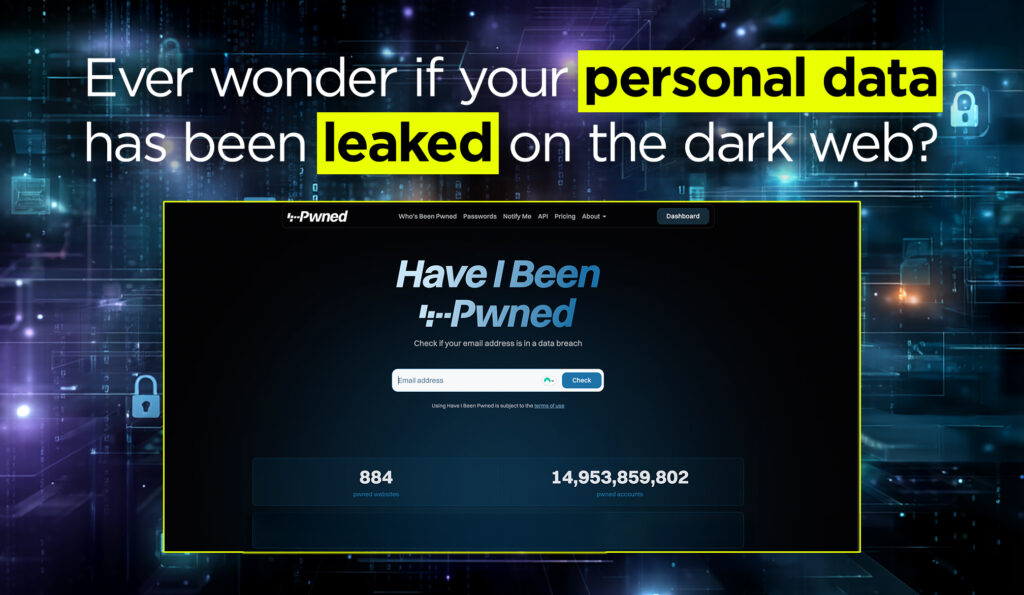
Haveibeenpwned.com, the popular website for checking if personal data has been exposed in data breaches, has launched a new version with a streamlined design, faster search, and improved monitoring tools.
When you enter your email address, the website checks it against a database of known breaches without storing information about your search.
And for searches of stolen passwords, it uses a technique called k-anonymity, which allows you to check if your password has been compromised without revealing the actual password to the website.
In this new version of the website, support for username and phone number searches has been removed.

Here’s an update on the story we covered earlier this year: the bankrupt DNA-testing firm 23andMe has agreed to sell its vast genetic database, which contains data from 15 million people, to drugmaker Regeneron.
While Regeneron promises to uphold existing privacy protections, consumers remain uneasy about the long-term use of their sensitive health data, especially following 23andMe’s data breach two years ago.
The New York Times reports that a court-appointed ombudsman will oversee the deal, but the sale puts renewed focus on how companies monetize personal DNA and whether consumer consent truly ensures lasting control.
These organizations say they have been hacked recently. If you do business with any of these companies, change your account password and use two-factor authentication wherever possible.

Phish of the Week
You get an urgent voicemail:
“Your subscription is about to renew, but your credit card was declined.
Call us immediately to update your payment.”
If you call the number and give them your card information,
you’ve just handed it to a scammer.
Click the button to listen to the voicemail.
Don’t even return the call. Delete the message.

One more thing...
Answers to Your
Cybersecurity Questions
“I read that virtually everyone’s social security number is available to hackers on the dark web. Do I even need to worry about this?”
A stolen Social Security number can be used to open financial accounts in your name, even if you’ve frozen your credit with the big three credit agencies, because many financial institutions don’t check your credit report when verifying your identity.
Gary Warner, Director of Research in Computer Forensics at the University of Alabama at Birmingham, says he recently received a tax form for $16,000 in transactions from a fraudulent CashApp account opened using his stolen data.
Though the platform ultimately confirmed the erroneous tax form wouldn’t be sent to the IRS, the discovery highlights how damaging and disruptive identity theft can be.
One lesson: freezing your credit isn’t enough. You also need to place a security freeze with ChexSystems (www.chexsystems.com/), which helps block new deposit or financial accounts from being opened in your name. It’s free to do this in most states, but some states allow a charge to lift the freeze temporarily.
Organizations like the Identity Theft Resource Center (www.idtheftcenter.org/) also offer free tools like Frozen Pii to help you place all necessary freezes.
“Your video about AI clones stealing our voices off social media posts has spooked me, so I’ve stopped posting videos on Facebook. Is there anything else I can do?”
Here’s guidance from Zander ID Theft Solutions: Take your voice off your voicemail greeting on your phone. When someone calls you and gets your voicemail, instead of hearing a prerecorded greeting of my voice saying “Hello this is Brian, leave a message”, etc.…now they just hear the automated “The person you are dialing is not available” message.
One less place that someone could try to clone someone’s voice.
“Sometimes, I see an orange dot at the top of my iPhone. What does that mean?”

If you notice a small orange dot at the top of your iPhone screen, it means an app is using your microphone. This dot doesn’t mean you’re being secretly recorded; it simply shows that the mic is active, often for expected reasons like voice messages, video recording, or voice search.
However, if the orange dot appears while you’re just scrolling or not using any audio features, it could mean an app has unnecessary access to your phone’s mic.
To check which app triggered it, swipe down from the top-right corner of your iPhone to open the Control Center. Then go to Settings > Privacy & Security > Microphone and turn off access for any app that doesn’t need it.
Cyber cartoon © 2025 Cartoonstock | Original content © 2025 Aware Force LLC
