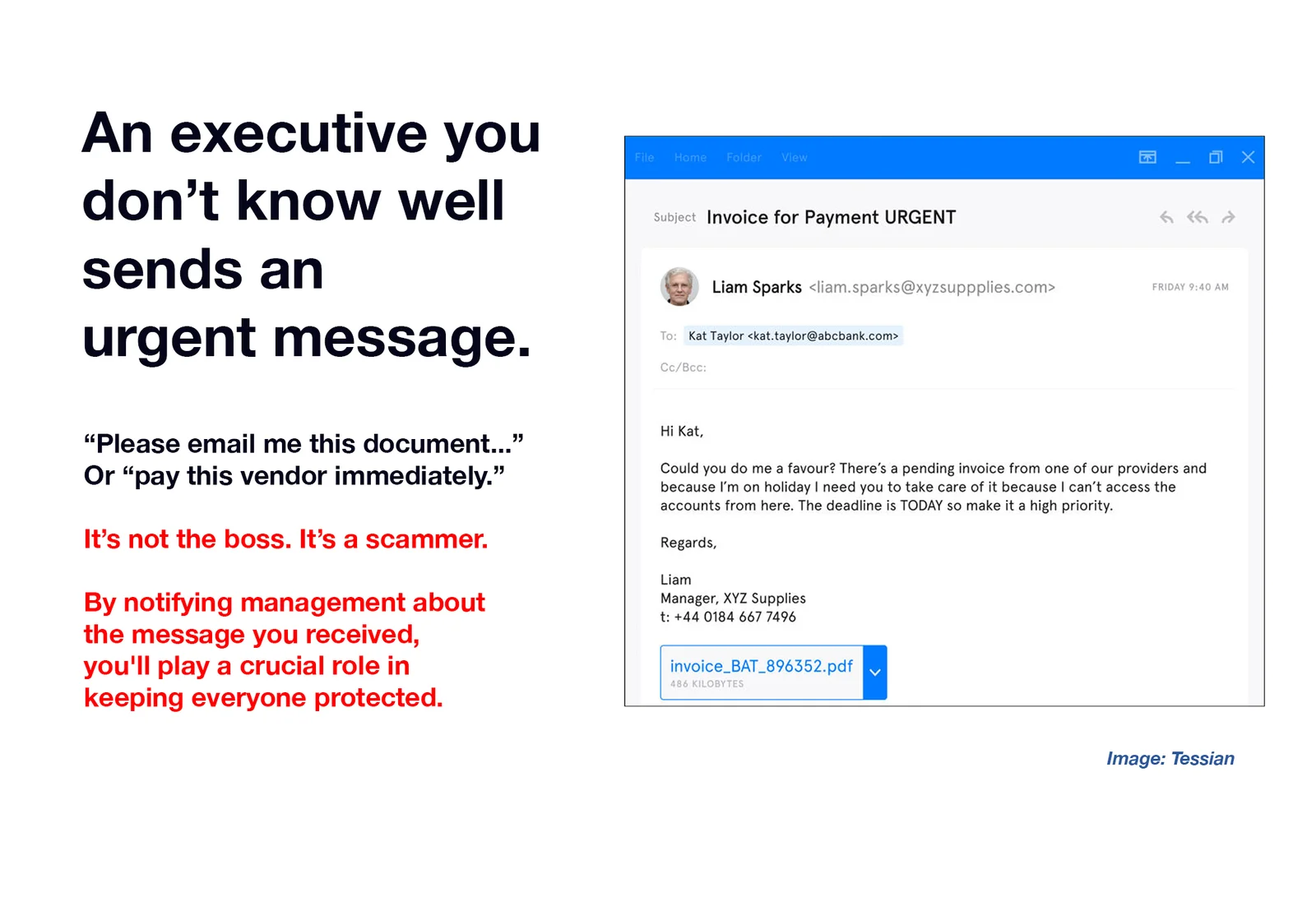
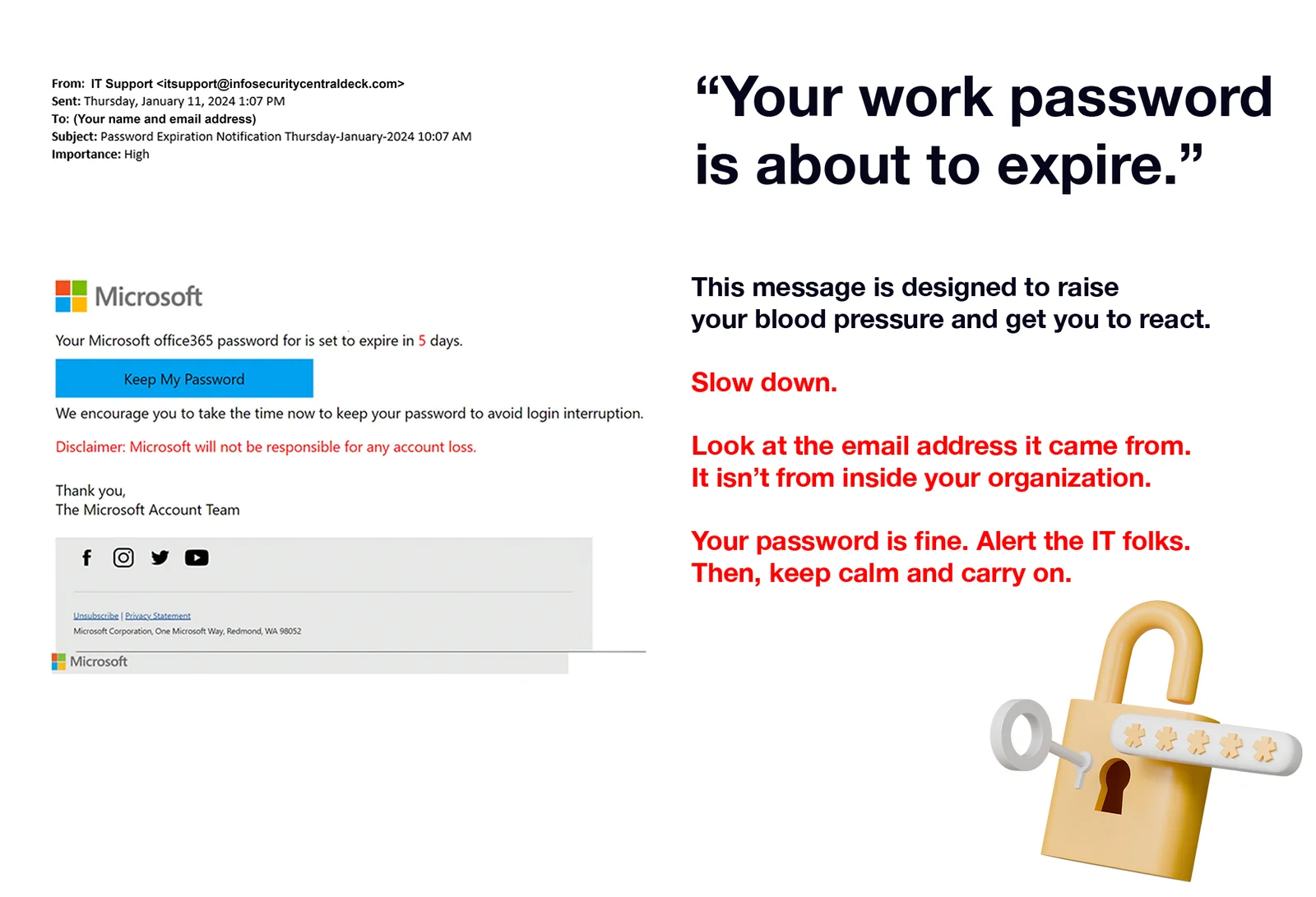
Cybersecurity News You Can Use

SECURING YOUR TEXT MESSAGES: The FBI is urging users to switch to encrypted messaging apps to protect text messages from hackers. Encryption means only the sender and the recipient can read the messages. Apple Messages, Google Messages, Signal, and WhatsApp provide encryption. Facebook Messenger, Instagram Direct Messages, Snapchat, and Telegram do not, nor does texting between an iPhone and an Android phone.
This warning follows reports of hackers infiltrating AT&T, Verizon, and T-Mobile in recent months, accessing customers’ call records and live calls.
Inc. says it’s also important to require a strong passcode to access your phone because if someone can gain access to your phone, it doesn’t matter whether your messages are encrypted.

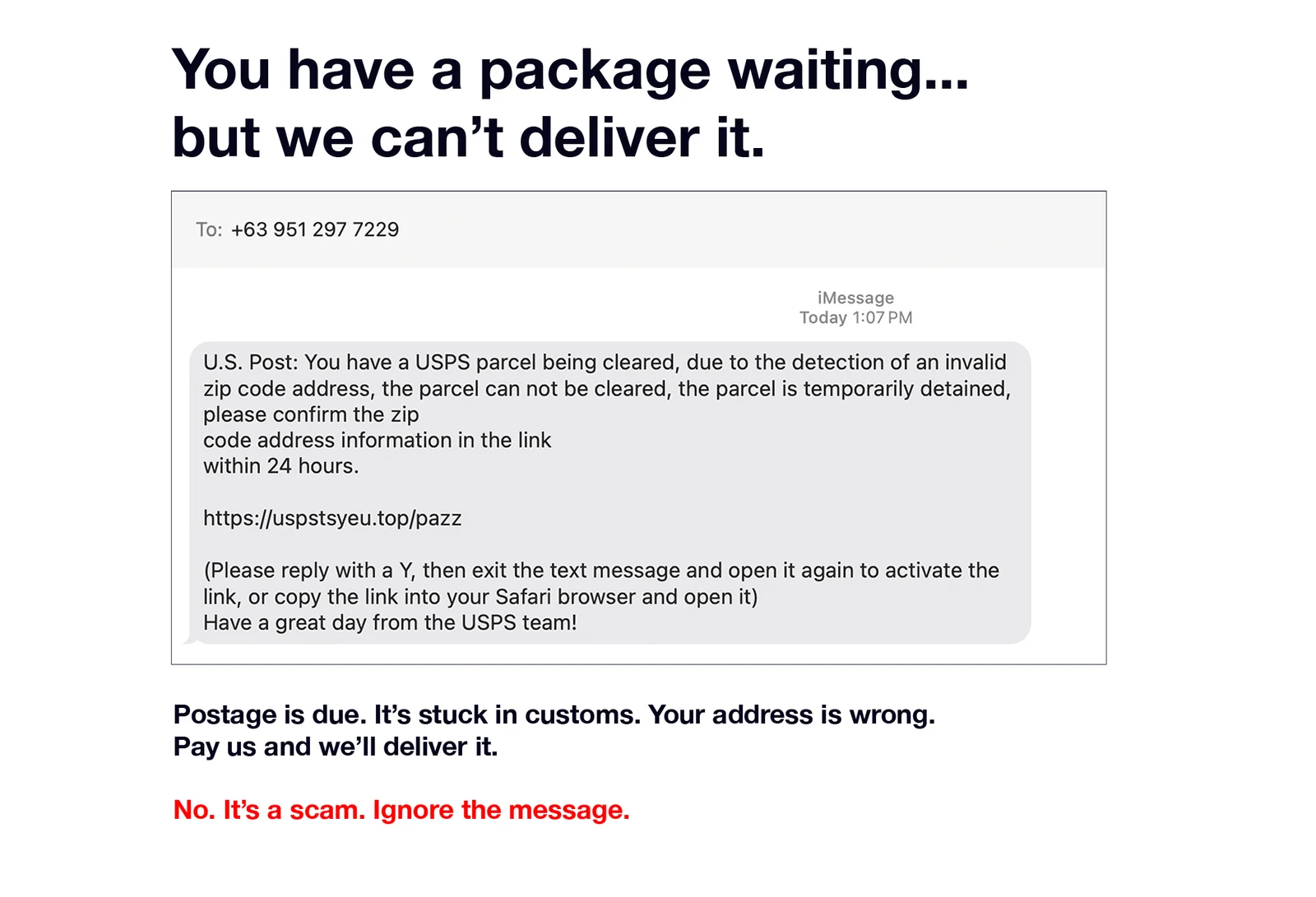
THAT URGENT TEXT ISN’T FROM NETFLIX: Bitdefender has uncovered a global phishing campaign targeting Netflix users aiming to steal login credentials, personal information, and credit card details. The campaign tries to trick users into believing their Netflix subscription is unpaid, and their account will be suspended. Victims receive a fake SMS instructing them to click a link to verify their account and update payment details. The information is then sold on the dark web.

JUST BECAUSE THAT PERSON ON SOCIAL MEDIA HAS A LOT OF FOLLOWERS… A UNESCO study concludes 2/3rds of social media influencers don’t fact-check before sharing information on social media, often trusting likes and views over evidence. The lesson: trending content in your social media feeds isn’t always reliable. Verify information independently, as your favorite influencers may prioritize popularity over accuracy.
![14 ai discount store [xsi]](https://cdn.awareforcecyber.com/wp-content/uploads/2024/12/14-AI-Discount-Store-XSI.png)
The "Hurry Up!" is a mental trigger. Its purpose is to rush you into taking action quickly before it's too late, likely causing you to overlook inconsistencies. Also, the countdown is probably fake.
AI has come a long way and is sometimes indistinguishable from reality. Train yourself to identify AI-generated content, it should be a massive red flag in situations like the example on this website.
A small company is running out of business and selling everything at a "steal." They might be trying to steal from you. Be suspicious: if it seems too good to be true, it probably is.
Scammers can easily populate their websites with fake reviews and even imitate external website reviews. To ensure legitimacy, go directly to review aggregators like Trustpilot and search for the vendor to find actual buyers' opinions.
Scammers might be reselling goods from reliable websites. Try to use a reverse image search tool like Google's, which might reveal that those same products cost a fraction of the price elsewhere.
By trying to appeal to the public as a legitimate small business, fraudsters aim to reassure their victims and induce belief. They will be available and friendly before the purchase, clarifying any questions. After you spend your money, they will disappear.

Guess the 5-letter cybersecurity word.
You have 5 tries.
Correct letter, correct spot.
Correct letter, incorrect spot.
Wrong letter.
Hint: A software update to fix security vulnerabilities.
Score: 0
One more thing...
What happens when you take advantage of an incredible deal on social media,
but the seller gets the last laugh?
This guy thought he was getting a big-screen TV for a cheap price.
But when he hooked it up, he discovered it was a fast-food menu display.
Clip via Instagram / andreaspoly
Original content © 2024 Aware Force LLC