




From the Cyber Newswire

NOT SO ANONYMOUS ANYMORE — Glassdoor.com has allowed current and former employees to post anonymous comments about their employers for years. But Wired says the rules are changing now: users must include their names in their profiles to ensure the contributor is employed at the business they’re commenting on. While they can generally keep their identities secret, there are cases where users’ names have been exposed without a way to undo the disclosure.

NOT THE KIND OF MOBILITY WE WANT — Following the leak of 73 million customers’ personal information, AT&T is forcing them to change their account passwords and urging them to monitor credit reports. The company says the exposed information is several years old and includes social security numbers. One takeaway from this breach: don’t automatically believe an unexpected text message claiming you must pay a past-due amount immediately.
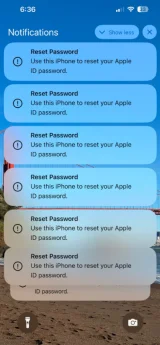
Screenshot by Krebs on Security
FAKE ALERT ON IPHONES — Krebs on Security says Apple customers have recently reported falling victim to sophisticated phishing attacks, which exploit a potential flaw in Apple’s password reset mechanism. In this scheme, the attackers manipulate Apple devices to generate numerous system-level prompts, rendering the devices unusable until the user responds with either “Allow” or “Don’t Allow” for each prompt. If the user navigates through these prompts without error, the scammers contact the victim, posing as Apple support on the caller ID. They claim the user’s account is threatened and request verification through a one-time code.

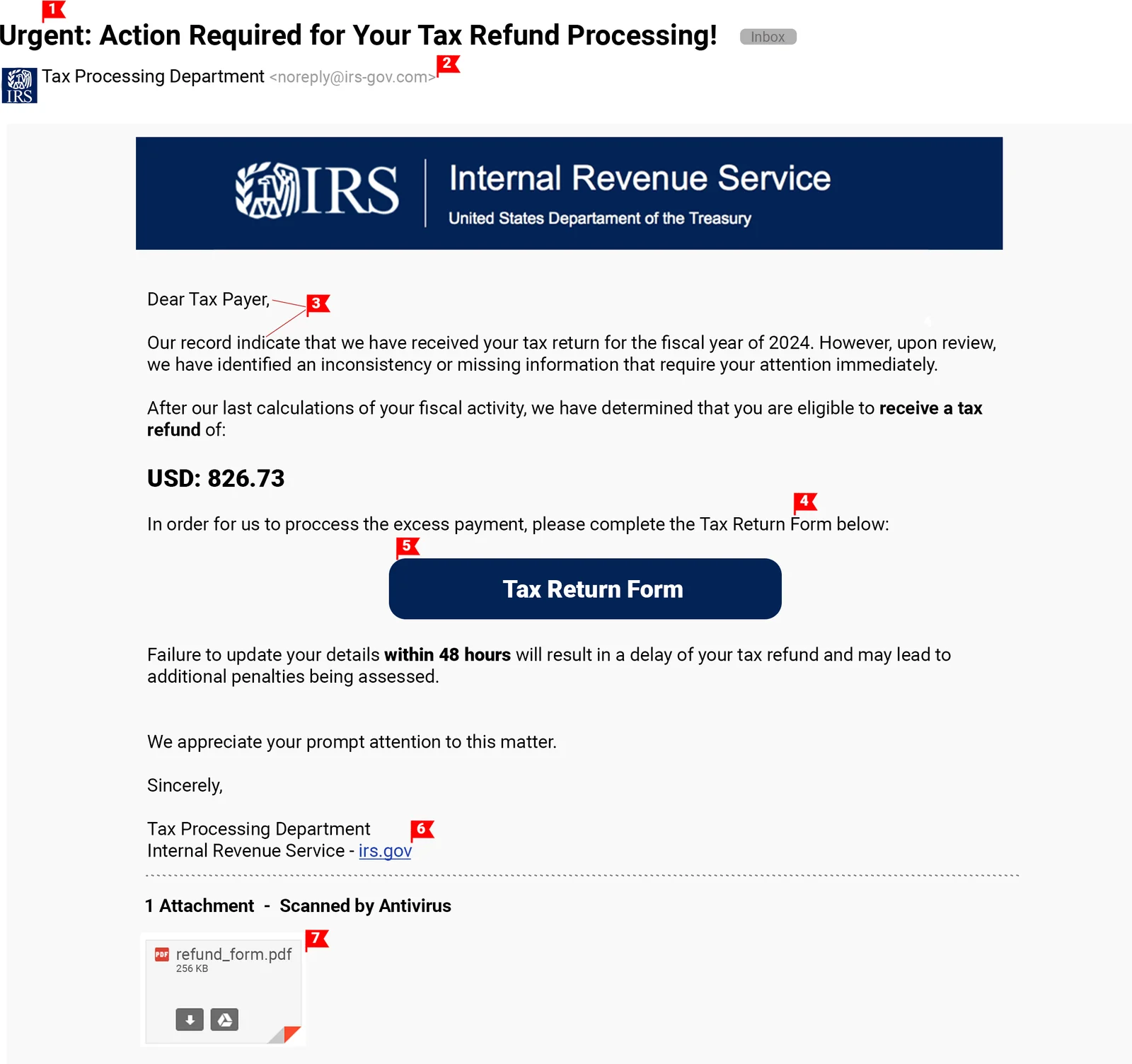
Urgent Call to Action: The email presses for immediate action. Scammers use urgency to rush you into making a mistake.
Suspicious Address: The IRS will not communicate with you via email. Besides, this address doesn’t seem legitimate.
Generic Text: The message seems generic, has no specific information about you or your taxes, and contains typos.
Request for Personal or Financial Information: The email's request to provide information is a classic sign of phishing.
External Link: The email includes a link. Upon inspection, the user would be able to notice it is a to non-government website.
Attention here: This seems like a link to the IRS page. ALWAYS HOVER OVER THE LINK to see the actual address it links to.
Attachments: This is a trap! Never trust files from unverified sources.
One more thing...

Answers to readers'
cybersecurity questions
“How do I know my text chats are private?”
“My wife downloaded a picture from an email she thought was from a legitimate sender. She immediately deleted the email when she saw the image was for a cryptocurrency company. She did not click on the image once it was loaded and did not click on any links. We did not see any new files in her downloads folder. She ran a Norton scan several times, but no threats were found. Can clicking download pictures to view email images cause issues (tracking pixels, malware, etc.)? Is there anything else that can be done besides a full scan?”
Generally, images downloaded from Google Search, Bing, Yahoo, and other search engines are safe. However, if you click on a linked website and download images, your computer could become infected with malware. Kudos to you for recognizing cryptocurrency as a risky topic and running an anti-virus app immediately when you suspected something was wrong. Sticking to reputable websites and running anti-virus programs are the most effective ways to protect yourself, particularly when dealing with your finances.
Both are good. Face ID is convenient. When you log in, you look at the phone; the scanning technology recognizes your face and grants you access. A long access code number is also effective if the numbers aren’t a pattern that’s easy to guess, like 123456. If you ever lose your phone, it is important to use one of those steps to protect your phone’s contents.
Cyber cartoon © 2024 Cartoonstock.com | Original content © 2024 Aware Force LLC