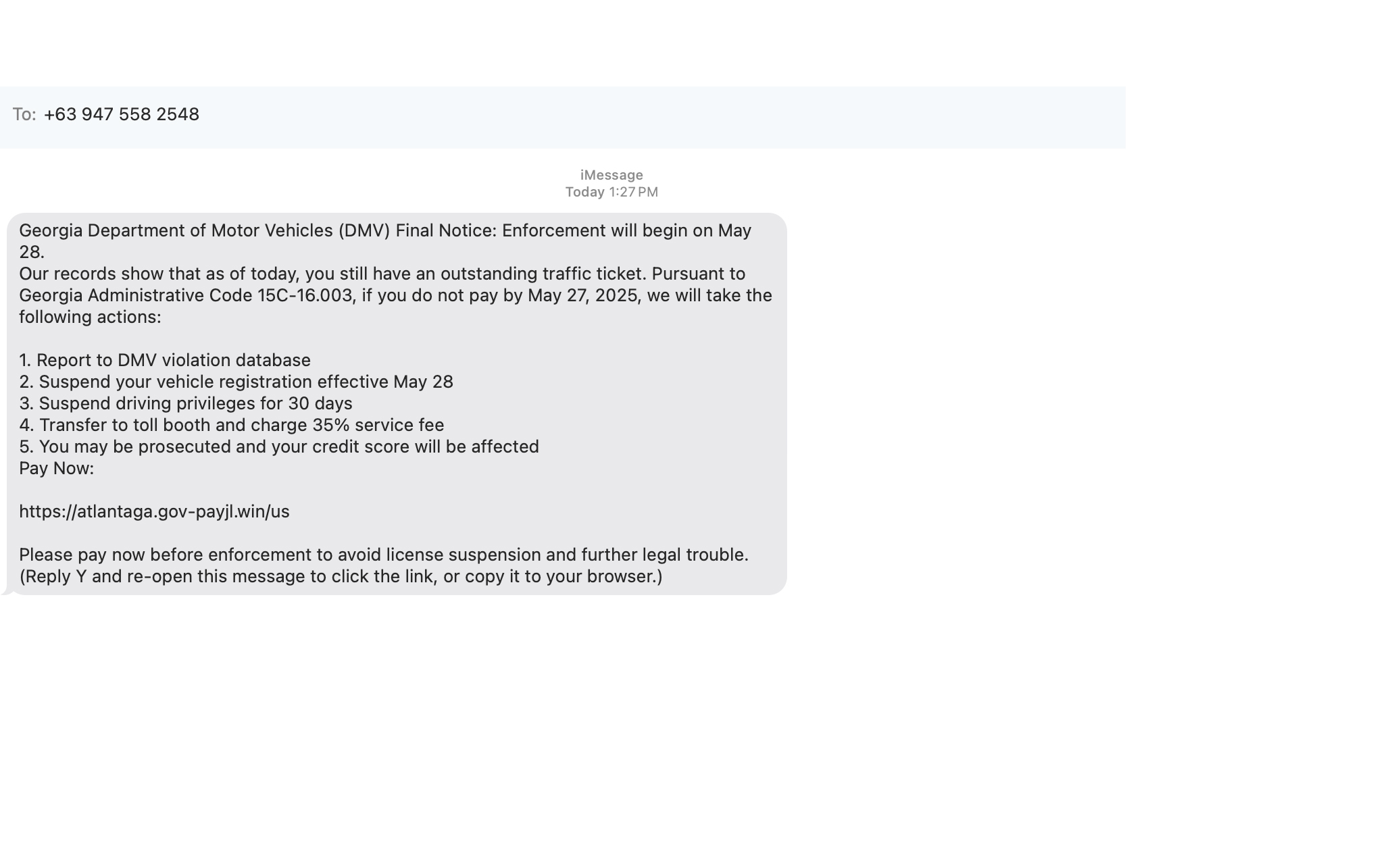
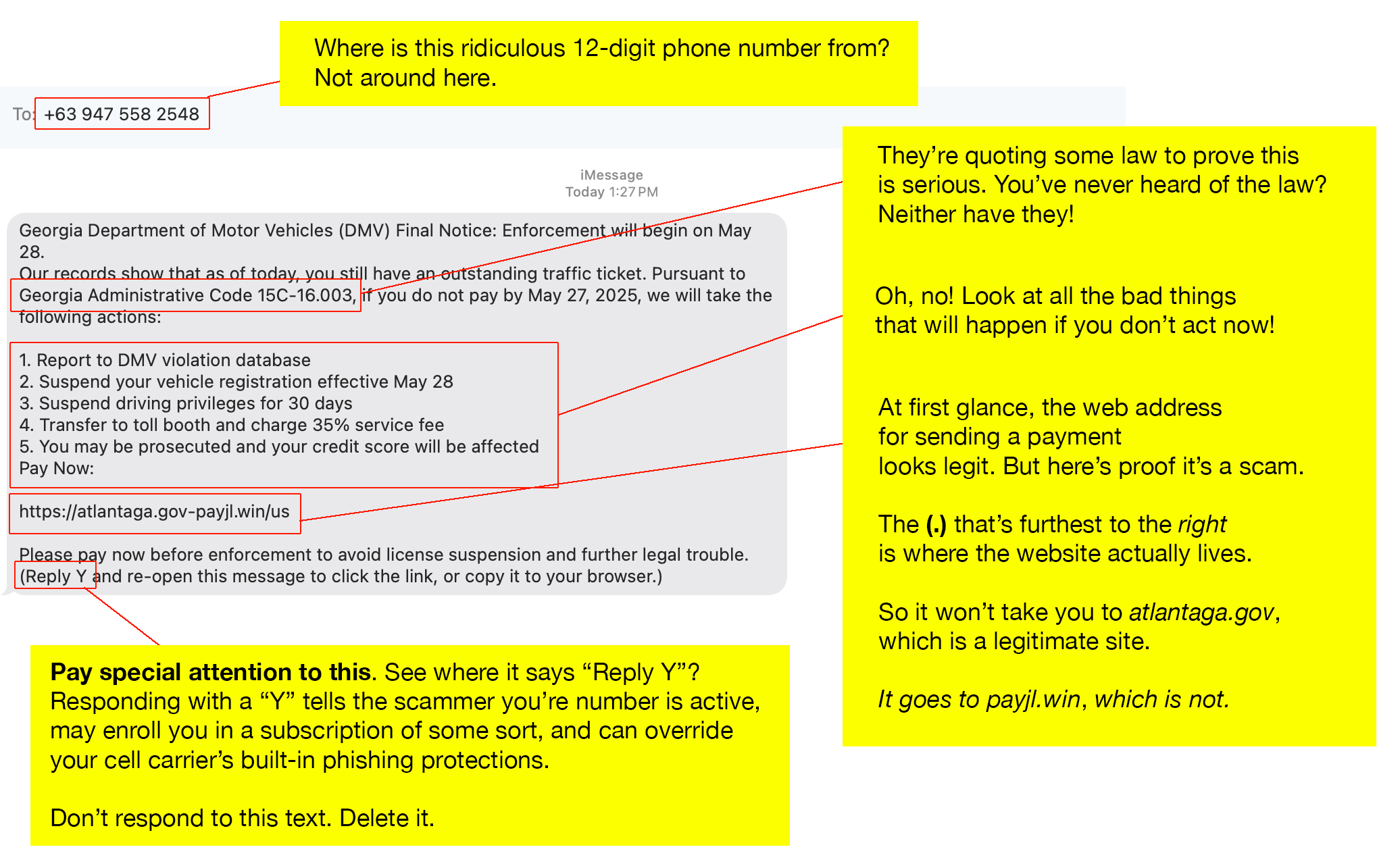
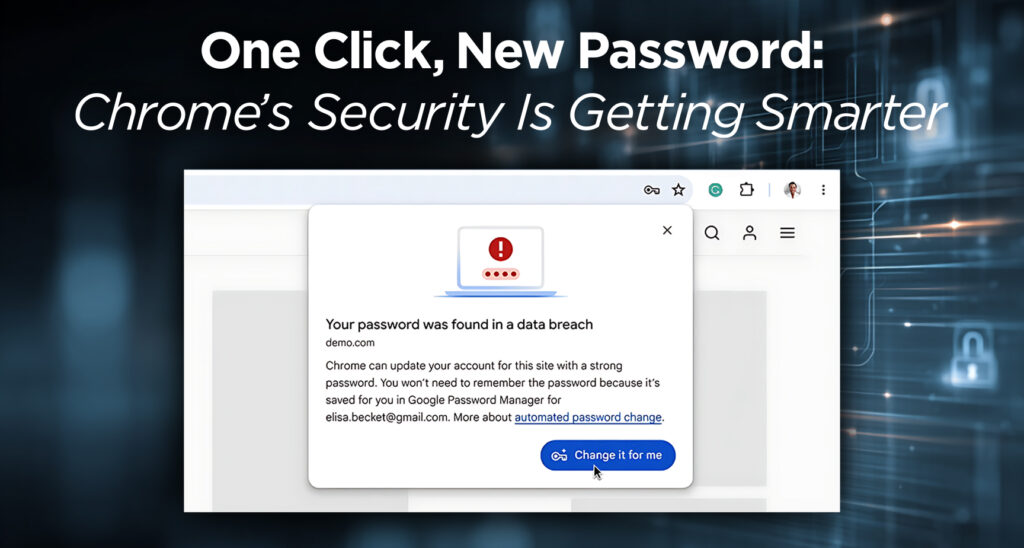
What to Guard: Your Digital Assets
Understand the key types of data that criminals target, and why they matter.
(Click cards to expand)
 Personal Info (PII)
Personal Info (PII)
What: Names, addresses, ID numbers – anything that identifies you.
How: Limit what you share, use privacy settings, guard personal documents.
 Financial Data
Financial Data
What: Credit card and bank account numbers, financial records.
How: Use secure (HTTPS🔒) sites/apps, never email banking details, monitor accounts.
 Login Credentials
Login Credentials
What: Passwords, PINs, authentication codes for accounts.
How: Enable 2FA, use strong unique passwords, use a secure password manager.
 Health Records
Health Records
What: Medical history, prescriptions, insurance info – highly sensitive.
How: Keep private, share via trusted channels only, use secure patient portals or encrypted files.
 Your Job’s Intellectual Property
Your Job’s Intellectual Property
What: Trade secrets, designs, client lists, strategy docs.
How: Limit access, encrypt files, label as confidential, use NDAs.
 Employee Information
Employee Information
What: Social Security numbers, salaries, contact & HR records.
How: Encrypt storage, restrict access, train HR, secure document disposal.