Phish of the Week
A common text and email scam from the past year involves fake package delivery attempts.
The message typically warns,
“We can’t deliver your package because your address information is incorrect.
Click here to update it and pay the amount due.”
Here’s a new version we’re seeing that’s even sneakier.
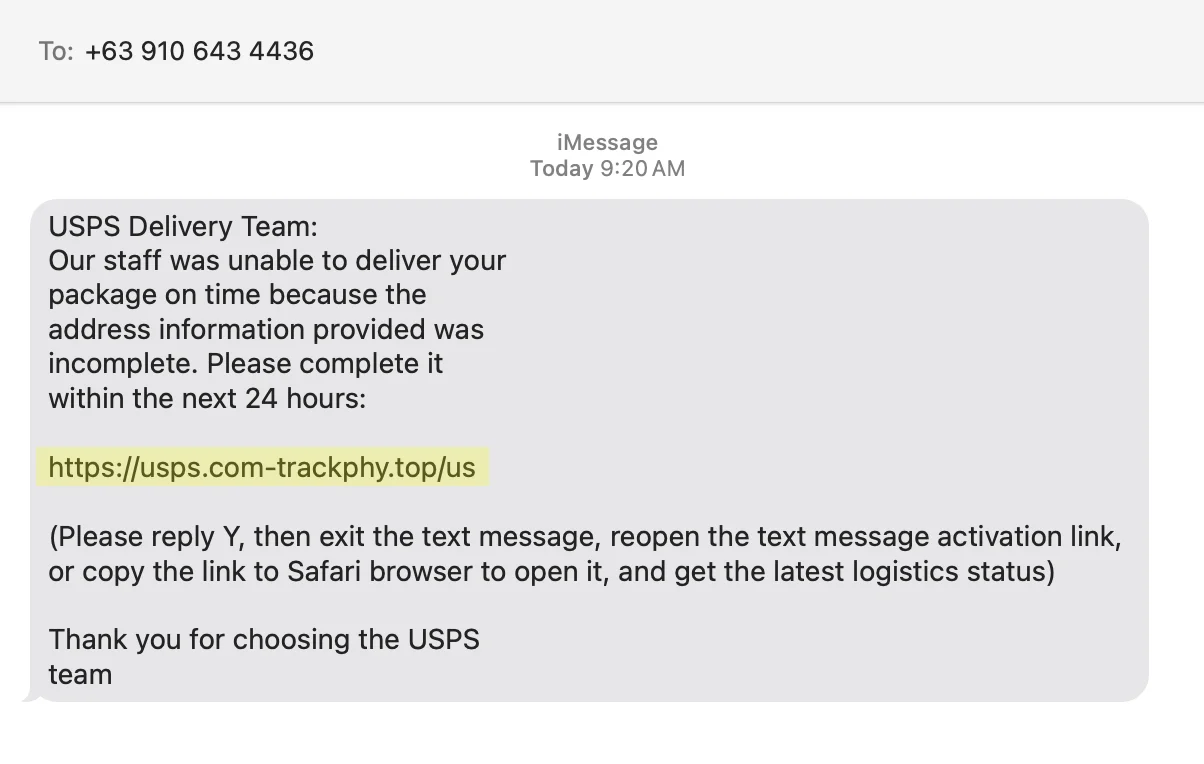
You have to look closely at the web address in the message.
It might look like the link goes to USPS.com. But, no.
The [.] that’s furthest to the right is actually where the link will take you.
That’s [.top], not USPS.com.
Sneaky!
Cybersecurity News You Can Use

LOCKING DOWN GIFT CARDS: Kroger food stores are piloting new anti-theft measures for gift cards in Louisville, Kentucky. The company has introduced locking pegs that require customers to pull cards through a narrow slot, making tampering significantly harder. According to the National Cybersecurity Alliance, international crime rings have been stealing gift cards, activating them, draining the funds, and returning the used cards to store shelves for unsuspecting customers to buy.

IS THAT SOCIAL MEDIA POST FROM A REAL PERSON? According to the Financial Times, Facebook and Instagram are set to feature more posts from AI-generated characters. These machine-created personas will come with “bios, profile photos, and distinct characteristics,” including racial and sexual identities designed to engage users. Early experiments revealed that these AI characters generated higher user engagement than real human accounts, leading to increased ad revenue for the platforms.
These organizations say they have been hacked recently. If you do business with any of these companies, change the password on your account and use two-factor authentication wherever possible.


One more thing...
“You should probably change your password.”
Here’s a routine from Michael McIntyre’s Netflix special, “Showman.”
Clip courtesy of Netflix
Answers to Your
Cybersecurity Questions
Would you advise setting up a guest Wi-Fi at home to help protect privacy and prevent introducing possible malware? I’ve always given guests access to my Wi-Fi without thinking about this.
— Heather D.
Yes, setting up a guest Wi-Fi network at home is a smart way to protect your privacy and prevent the spread of malware on computers, tablets, and phones in your home. A guest network creates a separate, isolated connection for visitors, so malware or malicious activity from an infected device stays confined to the guest network and doesn’t affect your main network.
You can change the guest network password or turn it off without impacting your devices.
To set one up, log in to the Wi-Fi router’s settings on your computer and look for the “Guest Network” option. Activate it and set a strong, unique password to prevent unauthorized access, even on the guest network.
How can someone with coding experience create a website that looks identical to another but hides malicious apps?
— JEvans
For skilled programmers, replicating a website’s design—its layout, colors, fonts, and overall appearance—is relatively simple. They can create a convincing copy and embed malicious code to steal passwords, credit card information, and other personal data.
What they can’t replicate, however, is the original website’s exact web address. Instead, they use fake addresses that closely resemble the real ones, hoping you won’t notice (e.g., “faceb00k.com” instead of “facebook.com”).
To protect yourself, always check web addresses carefully, update your web browser when asked, and use reliable antivirus software on your home computer.
Is it always safe to download extensions from an app store?
— AlwaysUnsure
Not entirely. While app stores like those run by Apple and Google screen for harmful apps and extensions, some dangerous ones can still slip through. When this happens, Apple and Google usually identify and disable them quickly.
For example, Ars Technica reports that nearly 1.5 million users downloaded malicious Chrome browser extensions from Google’s official app store before they were disabled.
Download apps and extensions only from official app stores or trusted online retailers like Microsoft and Adobe to stay safe. Stick to the software you genuinely need, and during installation, avoid granting permission to read or modify your data unless absolutely necessary.
Original content © 2025 Aware Force LLC